Hello everybody! :)
This blog post is an introduction of the organization I’ve been working with, The Tor project.
“ Privacy is a human right. We at Tor advance human rights and defend your privacy online through FOSS.”
The Tor Project works for advancements of human rights through free and open-source software.
We're becoming a world where most of our day-to-day activities are being shifted to the web. At such crucial times, digital privacy and security should be your outmost concern as it is equally important.
You might not be even aware about how much information you're giving access to over the internet. The targeted ads that follow for weeks clearly depicts, we’re being tracked at all times. It’s high time we redeem our rights, because privacy is a human right!
What is Tor?
Tor is a program that enables you to increase your digital privacy and security. It secures you by routing your connections via a distributed network of relays operated by volunteers across the globe. Tor aims to solve the main privacy problems - websites and other services can use your location to build databases about your habits and interests. Tor prevents this.
It avoids someone observing your Internet connection from learning the sites you visit and the sites you visit from discovering your actual location.
With Tor, your Internet connections don’t give you away by default - unless you provide (by filling out web/contact forms). Now you’ve the ability to control what and how much information you wish to reveal. The way most people use Tor is with the Tor Browser, which is based on Firefox ESR and comes bundled with privacy enhancing & anti-fingerprinting features.
How Tor works?
There’s this nice picture on the Tor Browser Manual that explains how the software functions:
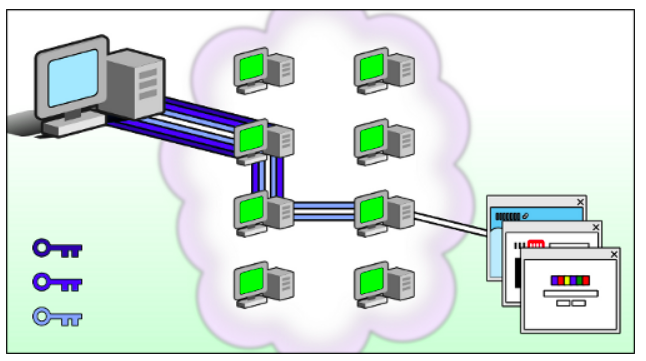
Tor works by sending your traffic through 3 random servers (also known as relays) in the Tor network. The green middle computers in the image above represent the relays. The first relay in the Tor network is called the Guard relay, the second is the Middle relay and third being the most important is the exit relay. The three keys represent the layers of encryption between the user and each relay.
It is the exit relay then sends the traffic out onto the public Internet. This means the website you’re visiting does not ever see you or your IP, instead only recieves the traffic from exit realys (as in the picture).
These relays are operated by volunteers based in different parts of the world. Since the IP of these relays is publicly listed, they can be blocked by governments or ISPs by blocklisting these IP addresses. Tor Browser includes tools for getting around these blocks. These tools are called pluggable transports which rely on bridges. Bridges are not listed publicly, so an adversary cannot identify them easily.
That’s a brief overview, so, defend yourself against surveillance! ;)